TECHNOLOGY
9 Game-Changing Tips to Ace Your Programming Assignment Like a Pro

Programming is a paramount skill in today’s technology-driven world. It empowers students to solve complex problems, create innovative software, and develop impactful digital solutions. As the foundation of fields like artificial intelligence, data science, and software development, programming enables students to shape the future of various industries.
According to the BBC, in 2024, the UK saw a nearly 10% rise in students applying for programming and computing courses compared to 2022. UCAS reported around 95,000 applications for computer and AI-related fields. So, pursuing a degree in this fast-growing field and writing programming assignments can be an uphill task.
Handling programming assignments can be tricky as it takes a mix of technical know-how, problem-solving skills, and solid time management. To make it easier, here are 9 practical tips to help you ace your assignments. Before delving into the strategies, you must first learn what a coding assignment is.
What is a Programming Assignment?
A programming or a coding assignment is any work or project that requires students to write and run computer code to solve a problem, create a program, or demonstrate a grasp of programming concepts. As per Pressbooks, coding assignments can involve simple programs or complex applications. Students should know how to deal with these kinds of assignments if they wish to finish them as well as possible.
You could be asked to provide content for the following platforms:
- Web: Web pages and web applications for browsers such as Firefox or Chrome
- Desktop: Desktop systems or apps for Windows, macOS, and Linux.
- Mobile: iOS and Android mobile apps.
How to Ace a Programming Assignment? 9 Effective Techniques
Programming assignments enhance fundamental coding skills and develop a deeper understanding of computational problem-solving. Completing these tasks creates the foundation for developing practical applications and solving business problems. Students who excel in their programming assignments stand out in the classroom and are well-prepared for successful careers in technology.
Programming assignments can sometimes be tough, and students often feel stress while dealing with this situation. If you are also one of them, you must get assistance from programming assignment writing services. They can guide you through the tricky parts and help you understand the technical concepts better so you can succeed academically.
Moreover, to help you succeed in your programming assignments, here are the 9 best tips and tricks to increase your coding skills and produce quality work.
1. Understand the Requirements
To be successful, the student should first focus on understanding the requirements of a programming assignment. To establish the main goals and expectations, the student should read through the work prompt at least several times. It is essential to divide the assignment into smaller, more doable chores and ask peers or teachers to help in any uncertain areas.
Students should be aware of important limitations, such as timeframes, programming languages, and data science, so they can write meaningful code, plan efficiently, and meet deadlines confidently.
Here are some important pointers to think about:
Read Carefully
The problem statement constitutes the heart of the assignment. To completely comprehend what has been required, re-read this more than once or twice. Students should note all specific requirements of the statement, particularly their specific terms and phrases.
Break it Down into Core Elements
Break problem statements into digestible chunks of work. Break down the input and output as well as particular criteria, especially if restrictions were highlighted during the request.
Identify Limitations
The difficulty of time or the requirement for particular techniques are a few examples of restrictions. Be sure you are aware of the limit you are dealing with.
It’s time to examine the requirements after you have a firm grasp of the problem description.
The following are some topics to think about:
- What is the program’s objective? What is the intended purpose of the program? What issue is it attempting to resolve?
- Which inputs and outputs are there? What information will the program receive, and what will it output?
- Which data structures and algorithms are necessary? Does the problem require the use of specific data structures or algorithms?
- Are there specific constraints or requirements? Are there specific conditions or constraints that must be met, such as time or space complexity?
2. Plan Before You Code
It is exciting to start any new coding project; however, it can quickly get disorganised, or you may lose focus if it is not well-planned. Effective planning is essential to software development because it puts you in a better position to guarantee that your project will stay on course and, as a result, accomplish its goal.
Moreover, by making a plan, your code will be organised, effective, and error-free. The eight easy steps recommended by Northcoders can help you organise coding efficiently. It’s important to think through your strategy properly before actually coding the real programming assignment.
Describe the Problem
Start by understanding the problem you are trying to solve. Clearly state the project’s purpose, audience, and expected outcome. This will frame the entire planning process.
Set Clear Objectives
Establish the exact objectives you want to achieve with your project. Specific goals help to maintain focus and effectively track your progress.
Establish the Needs
List down the features and functionalities that your project needs. To make the development process more manageable, split them into smaller activities that can be done separately.
Create a Schedule
Make a project schedule that will include due dates and milestones for every stage. This will ensure consistent progress and keep you organised.
Create Architecture
Plan your project’s architecture, considering data flow, user interface layout, and database design. A well-thought-out architecture enables effective development.
Choose Tech Stack
Select the best tool, framework, and programming language for your Java programming assignment. The choice of technology stack can make a huge difference in the success of the project.
Divide Work
Divide the project into smaller tasks. To promote accountability and teamwork, assign each task to a specific developer or team member.
Allocate Resources
Ascertain the necessary hardware and software resources. Make sure you have everything you need to carry out the strategy without a pitfall.
3. Research and Gather Resources
Effective study and resource gathering are necessary to finish a C- Programming assignment because they guarantee that you comprehend the concepts and can apply them effectively. The below-mentioned techniques will help you do very well on your programming projects:
Investigate Effectively
- Determine the Ideas: First, define the specific programming concepts, kinds of algorithms, data structures, or specific programming languages such as Python or Java relevant to the assignment.
- Use Reliable Sources: Look for reliable sources, such as scholarly publications, online courses, and textbooks.
- Review the Documentation: Learn the official documentation for the framework or programming language you are using. This is often the most authoritative source for functions, libraries, and best practices.
Gather Resources
- Online Forums and Communities: Students must check online forums and communities like Reddit’s programming subreddits or Stack Overflow. On these platforms, you can ask your concerns and get answers from experienced developers who have dealt with similar issues.
- Tutorial Videos: Use YouTube and other websites to locate video tutorials that visually explain complex subjects. This can be extremely helpful in understanding debugging procedures or coding strategies.
- Code repositories: Look at GitHub to discover open-source projects related to the task at hand. Reading the code helps you understand existing coding styles and ways to solve problems.
4. Start Early
One of the most important ways to ace a programming assignment is to start early. By starting before the deadline, students give themselves enough time to understand the criteria, conduct research, and break down the tasks. Students who plan can avoid doing assignments in a rush, which often results in mistakes or incomplete work.
Furthermore, it allows time for the logic of the program, testing out different solutions and debugging code. Starting earlier to write an assignment instils confidence, hence reducing the anxiety brought about by last-minute performance.
Also, beginning work earlier provides sufficient time for correcting the challenges faced by the student to present it to the public and seeking help from fellow mates, lecturers, and other people through the internet if challenges arise.
5. Write Clean Code
As per freeCodeCamp, clean code is computer code that is easy to comprehend and read. Simple, clear, and expressive code should be written cleanly. It follows a set of norms, guidelines, and procedures that make it easy to read and comprehend. To complete a programming task correctly, you should write clean code. Clean code makes it easier to work within a team.
The following best practices suggested by GeeksforGeeks will help you write clear code that will improve your coding skills and amaze your instructors:
Use Meaningful Names
You will need to write names for variables, classes, opinions, modules, packages, manuals, and other items. Students must cultivate the habit of giving meaningful names to their code. The three goals of any name you use in your code should be what it does, why it exists, and how it is used.
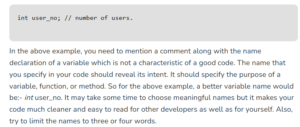
For example:
Image Source: GeeksforGeeks
The Single Responsibility Principle
In any programming language, classes, operations and approaches are helpful for code organisation. So, when composing code, it’s time to think about how a function should be designed, such that it is the most effective in representing itself. Most beginners do this by writing a function that can do everything as if it could manage to finish nearly everything.
Do Not Write Trivial Comments
Developers often use statements to indicate the nature of a line of code in their online programming assignments. Indeed, comments help to describe the code and what it does. However, it also means that the code requires additional maintenance. The code moves around during development, but when a comment remains in the same spot, it might cause significant problems.
In addition, on account of such useless comments, students will get puzzled and deviated. The syntax of modern programming languages is much like that of the English language, which is all you need to explain the intention of a line in your code. So, students must give their variables, methods, and files meaningful names to help them avoid using comments in their code.
Write Human-Readable Code
Many students especially beginners make incorrect code because of writing everything in one line without using line breaks, proper use of whitespace or indentation. They end up with a cluttered disorganised code very hard to maintain.
Remember, your code’s appearance matters-always. What people recall about a particular software developer is the coding style students follow in their code.
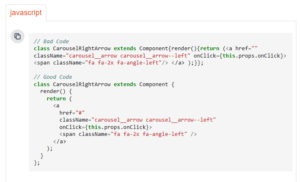
Image Source: GeeksforGeeks
Create Unit Tests
In development, writing unit tests is crucial. It improves the readability, flexibility, and maintainability of your code. It gets simpler to make code modifications and minimise errors. In line with BrowserStack, Test Driven Development (TDD) is a software development strategy that emphasises writing unit test cases before composing genuine code. It combines recomponenting, unit testing, and programming.
6. Test as You Go
A key strategy for completing MATLAB programming assignments is testing as you go. This approach underscores the importance of writing tests at every stage of the development process to guarantee that your code does what it is supposed to do and meets the requirements of an assignment.
Here’s how to do this strategy in practice:
Putting Testing Into Practice as You Go
Implement TDD
One of the TDD software development techniques is that tests are written before real code is written. There are three core steps in this cycle, and they are:
- Red: Verify that the feature has not been implemented by writing a test for a certain functionality that fails in the very beginning.
- Green: Not too much code should be implemented so that it just can pass the test. It is just what is required so that it can meet test requirements.
- Refactor: Clean up and optimise your code without changing its outward behaviour once the test is successful. This step ensures that your code will continue to be readable and effective.
Start Small
Start by testing small features or parts of your application. For example, when building a calculator application, start by writing tests for addition and subtraction before moving on to more complex capabilities.
Use Automated Testing Tools
Use testing frameworks and tools appropriate for the programming language you are using. According to Staragile, the software testing tool Selenium offers a robust, open-source framework for automating web applications across numerous platforms and browsers. Because of its adaptability, testers may write scripts in several computer languages, such as C#, Python, and Java.
Create Descriptive Tests
Ensure the names of your tests tell everyone exactly what the test is verifying. This technique makes tests easier to read and easier for you or others to quickly understand what each test intends to check.
Testing as you go would also do for you to ensure that your code meets requirements. Ultimately, this proactive approach translates into more reliable, maintainable code and increased self-assurance in your programming assignments.
7. Use Version Control
The use of version control is essential in completing a programming assignment. Throughout the development process, it allows you to interact efficiently, track changes, and preserve the integrity of your code.
You can ace your programming assignment by applying version control in the following ways recommended by DEV Community:
Easy to Track Changes
Version control systems have made keeping track of all the changes in your code easy to do. They are actually set up to store versions of the code that you write into a repository; thus, you can compare different versions and notice what changes. Debugging and fixing across versions could be highly enhanced by that.
Better Collaboration
Version control systems make it easy for several developers to work together on a project. Each developer can achieve their modifications to the repository and keep their copy of the source. This makes it easier for other innovators to review and accept the changes.
Easier to Roll Back Changes
Version control systems make it easier to back modifications to an earlier version of the code if you make a mistake. Since you won’t have to go back and undo any changes you’ve made, this can save you a ton of time and work.
Greater Reliability
Version control solutions assure you that your code will always be backed up and safe. If your PC goes wrong, you can easily retrieve your code from the repository, greatly reducing the chances of losing any of your work.
Improved Organisation
Version control solutions assist you in maintaining the organisation of your code. Branches can be made for various features or problem fixes, and switching between them is simple. This greatly facilitates maintaining the organisation and maintainability of your code.
Developers can get several advantages from using a version control system. It not only makes it easier to monitor changes but also improves the reliability and structure of your code when working with other developers. A version control system is absolutely something you should consider if you don’t already have one.
8. Refactor and Optimise
To finish a programming assignment well, you must refactor and optimise your code. These processes improve the quality of your code, increasing its performance and maintainability.
Let’s examine each of these methods one by one which Code Conquest suggests:
Extract Functions and Methods
You should move a code snippet into a new method or function if it may be combined. The more lines a code snippet contains, the harder it is to understand. Thus, students could use the code that executes a particular task to develop functions.
Split Temporary Variable
In a function, there can be a local variable that’s used to store different intermediate values. In that case, you can use different variables for different values where each variable holds only one value.
Variables Extracted from Expressions
If you’ve got a hard-to-understand expression, you could substitute self-explanatory variables for its components.
Inline Substitute the Temporary Variables
Avoid using temporary variables if your methods just execute one statement and return the value.
Combine Conditional Expressions into One
If several conditional expressions produce the same result, students can combine all of the conditions into a single expression. This will help eliminate redundant code.
Strategies for Optimisation
- Examine performance snags: Use profiling tools to find slow or ineffective parts of your code. Concentrate on optimising these parts to increase overall performance without compromising readability.
- Employ Data Structures That Are Effective: Depending on your particular use case, select data structures that maximise performance. For instance, speed can be greatly increased by using a hash table rather than a list for fast lookups.
- Reduce Resource Intensity: Students should optimise algorithms to increase efficiency in terms of processing time or memory usage. This means eliminating unnecessary calculations within a loop or using a superior algorithm.
9. Seek Feedback
A key strategy in succeeding on a programming assignment is asking for feedback. By doing so, students can improve the quality of their code by asking their lecturer, their peers, or other members of online coding forums for constructive criticism. Moreover, it allows you to recognise mistakes, enhance your reasoning, and ensure that your answer follows the assignment requirements.
However, if you are not able to grasp certain parts of the task, you can get professional help from top-rated assignment writing firms in the UK to understand difficult concepts and, hence, complete your programming task with optimum productivity. By incorporating expert aid with multi-source feedback, you can enhance your academic achievement and coding skills.
End Note
Programming assignments require more than technical expertise to master. Students need proactive thinking, efficiency in using resources, and planning. Putting all nine critical suggestions into play may enhance coding skills and shorten the workflow, from breaking hard work into smaller parts to finding people who give positive criticism or using websites as resource persons.
Remember that success in programming requires consistent practice and being open to grow with mistakes. Adopt these techniques, maintain your curiosity, and celebrate your development as a programmer. So, put these pointers into practice right now to improve your assignments and advance in your coding career!
TECHNOLOGY
Top 3D Printing Trends to Design Highlighted by 3D659.com Blog

Dive deeper into the possibilities with 3D659.com Blog. 3D printing continues to redefine innovation, offering groundbreaking applications across industries like healthcare, automotive, fashion, and education. With new technologies emerging and design capabilities expanding, keeping up with the latest trends is essential for designers, engineers, entrepreneurs, and anyone captivated by this versatile technology.
This blog explores the top trends in 3D printing and design shaping 2024. Whether you’re a professional in the field or simply curious about the evolution of additive manufacturing, you’ll gain insights into emerging technologies, sustainable practices, and creative applications. Let’s explore the future of 3D printing together.
What’s Driving Innovation in 3D Printing by 3D659.com Blog?
The meteoric rise of 3D printing stems from its ability to iterate designs, drastically reduce production costs, and produce highly customized solutions. But what trends are taking center stage in 2024? Here’s what to watch:
1. Sustainability in 3D Printing
Sustainability is no longer a buzzword—it has become a driving force in 3D printing. From materials to processes, the industry is turning to eco-friendly solutions.
- Biodegradable Filaments: PLA filaments derived from cornstarch remain popular, but newer biodegradable materials such as hemp-based filaments are emerging.
- Upcycling Waste: Companies like Reflow are producing materials from recycled plastic waste, reducing environmental impact.
- Energy-Efficient Designs: With advanced algorithms, new designs prioritize minimal material use, reducing energy and material waste.
For industries like fashion and automotive, 3D printing is proving pivotal in creating sustainable prototypes and products.
2. Widespread Adoption of Metal 3D Printing
Metal 3D printing has long been limited to specialized industries due to cost and complexity. However, it’s rapidly entering mainstream manufacturing.
- Key Sectors Benefiting:
- Aerospace: Lightweight metal parts maintain strength without compromising fuel efficiency.
- Healthcare: High-precision implants and custom prosthetics are crafted using biocompatible metals.
- Lower Costs: Advancements in Direct Metal Laser Sintering (DMLS) and Electron Beam Melting (EBM) are making metal printing more affordable for smaller businesses.
The accessibility of metal 3D printing is set to revolutionize precision manufacturing.
3. AI-Powered Design Automation
Artificial intelligence is transforming 3D printing design. By automating design-to-print processes, AI simplifies workflows while improving creativity.
- Generative Design: AI tools allow designers to input specific objectives and constraints, enabling the software to generate optimal designs. Companies like Autodesk are spearheading this movement.
- Error Simulation: Before printing begins, AI-powered software identifies potential errors, saving time and resources.
This integration of AI empowers businesses by streamlining complex tasks without compromising design precision.
4. Multi-Material Printing
Gone are the days of printing with a single material. Multi-material printing is taking additive manufacturing to the next level by combining various physical properties in a single print.
- Examples of Applications:
- Medical Devices: Print objects with rigid internal support and flexible exterior parts for prosthetics.
- Electronics: Integrate conductive and insulating materials into one 3D-printed circuit.
This technology opens new doors for designers bridging the gap between creativity and functionality.
5. 3D Printing in Healthcare
Perhaps no sector has benefited from 3D printing as much as healthcare. The technology is transforming patient care by delivering personalized, precise solutions.
- Individualized Medical Devices: Orthopedic implants, hearing aids, and dental fixtures achieve perfect fits tailored to the patient.
- Bioprinting Progress: Researchers are advancing bioprinting to develop tissue scaffolds and organ prototypes promising future healthcare breakthroughs.
For healthcare professionals, 3D printing translates into more effective treatments and improved patient outcomes.
6. Large-Scale 3D Printing
Building on its ability to produce small-scale parts, 3D printing is now scaling up. Large-scale printers produce objects for automotive, aerospace, and construction industries.
- Printed Homes: Companies like ICON are using 3D printing to construct homes in under 24 hours, reducing labor costs and providing innovative housing solutions.
- Transportation Prototypes: Oversized components for cars, buses, and airplanes benefit from the precision provided by large-format printers.
This shift towards grander projects expands the potential impact of additive manufacturing globally.
7. Custom Consumer Products
Personalization in products is in high demand, and 3D printing is leading the way in delivering tailored goods.
- Applications Include:
- Custom-fit footwear designed using precise scans of individual feet.
- One-of-a-kind fashion accessories created to match consumer preferences.
- Décor and furniture pieces with unique, intricate designs customized for specific spaces.
For entrepreneurs, offering custom 3D-printed goods presents immense opportunities for differentiation.
8. Education and Open-Source Collaboration
Educational and collaborative advancements are nurturing innovation. Open-source initiatives have democratized 3D printing by 3D659.com Blog, making it accessible to more people and fostering creative communities.
- Education Efforts: Introducing additive manufacturing in schools provides younger generations with valuable skills for the future economy.
- Open-Source Designs: Platforms like Thingiverse allow designers to share ideas, creating endless possibilities for iteration and improvement.
These movements ensure that creativity and accessibility grow hand-in-hand.
9. New Printable Materials
Material innovation continues to expand the 3D printing horizon. Some of this year’s breakout materials include:
- Flexible Thermoplastics: Perfect for applications like wearables and medical devices.
- Ceramic Filaments: Durable and heat-resistant, making them ideal for engineering projects.
- Graphene-Infused Resins: Exceptional conductivity opens possibilities for electronics and sensors.
The constant introduction of new materials ensures additive manufacturing remains on the cutting edge.
What Trends Mean for Your Business
Whether you’re a small entrepreneur prototyping custom goods or a large corporation optimizing production, these 3D printing trends can drive significant value. Leveraging even one or two advancements—such as sustainable materials or personalized designs—can set your business apart in an increasingly competitive landscape.
Change is inevitable in additive manufacturing, and those ready to innovate will undoubtedly reap the rewards. Are you prepared to take the leap?
Take the Next Step in 3D Printing Innovation
The trends above highlight only a fraction of what’s in store for 3D printing in 2024. Continuous research, collaboration, and experimentation are key to unlocking the technology’s full potential.
Dive deeper into the possibilities with 3D659.com Blog. Explore even more insights, expert tips, and cutting-edge news to stay ahead in the world of 3D printing and design. Visit 3D659.com and get inspired today.
TECHNOLOGY
The Future of Chas6d: Trends and Predictions to Watch For

Introduction to Chas6d and its current state
Chas6d is making waves in the digital landscape, capturing attention and sparking conversations worldwide. As we stand at the crossroads of innovation and technology, understanding Chas6d’s current state is crucial for anyone looking to navigate this exciting terrain. With a blend of cutting-edge advancements and evolving consumer preferences, the future holds immense potential for growth and transformation within the Chas6d ecosystem. Let’s dive into what lies ahead—trends shaping its journey, predictions on its evolution, challenges to tackle, and how consumer behavior will play a pivotal role in defining its success. The road ahead promises to be anything but ordinary!
Technology Trends Impacting the Future of Chas6d
Emerging technologies are reshaping Chas6d’s landscape. Artificial Intelligence is at the forefront, enhancing decision-making processes and personalizing user experiences. Machine learning algorithms can analyze vast data sets, predicting trends before they emerge.
Blockchain technology also plays a significant role in ensuring transparency and security for transactions within Chas6d. It builds trust among users by providing an immutable record of all interactions.
Additionally, the rise of Internet of Things (IoT) devices means more connectivity. This allows for seamless integration with everyday life. Users expect their digital platforms to be intuitive and responsive.
Moreover, advancements in cloud computing offer scalability solutions that benefit both developers and consumers alike. With increased storage capacity and processing power, Chas6d can accommodate growing user demands effortlessly.
These technological shifts are not just changing how businesses operate; they’re redefining consumer expectations across the board.
Predictions for the Growth and Evolution of Chas6d
Chas6d is poised for substantial growth in the coming years. As technology evolves, so too will its capabilities. Enhanced user experiences and personalized offerings are on the horizon.
The integration of artificial intelligence into Chas6d will likely transform how users interact with the platform. Expect smarter recommendations and more intuitive interfaces that adapt to individual preferences.
Additionally, we can anticipate an expansion into new markets. This might involve collaborations or partnerships that broaden its reach across various industries.
Sustainability is another key factor driving future developments within Chas6d. Emphasis on eco-friendly practices could attract a more conscious consumer base, contributing to both brand loyalty and growth.
As data privacy concerns rise, Chas6d must innovate while ensuring user trust remains intact. Transparent practices will be critical in fostering long-term relationships with customers as it navigates this evolving landscape.
Potential Challenges and Solutions for Chas6d’s Future Success
As Chas6d navigates its future, several challenges loom on the horizon. Competition is intensifying, with new players emerging almost daily. Staying ahead will require continuous innovation.
Another hurdle is adapting to changing regulations and compliance standards. The industry landscape can shift overnight, demanding agility from companies like Chas6d.
Consumer trust is also a critical factor. Maintaining transparency and accountability can help foster loyalty amidst skepticism in today’s market.
To tackle these issues head-on, investing in research and development is essential. Exploring partnerships or collaborations could provide fresh perspectives and resources for growth.
Embracing customer feedback loops will allow Chas6d to respond swiftly to consumer needs while enhancing product offerings. By prioritizing adaptability, the company can carve out a sustainable path forward despite potential setbacks.
Case Studies of Other Companies with Similar Trajectories
Examining the journeys of companies like Airbnb and Uber reveals valuable insights for Chas6d. Both faced initial skepticism but ultimately transformed their respective industries through innovation and adaptability.
Airbnb started as a simple room-sharing platform. It now dominates global travel by embracing technology and prioritizing user experience. Their focus on community-building has set a standard that resonates with consumers, highlighting the importance of creating connections.
Uber disrupted traditional transportation models by leveraging mobile apps and real-time data. Its rapid growth relied on understanding consumer needs while navigating regulatory challenges. This approach showcases how flexibility is crucial in evolving markets.
Similarly, Chas6d can learn from these experiences to carve its path forward. By fostering innovation and remaining responsive to market trends, it may unlock new opportunities for success in an ever-changing landscape.
The Role of Consumer Behavior in Shaping the Future of Chas6d
Consumer behavior is a powerful force driving the evolution of Chas6d. As preferences shift, companies must adapt to meet new demands.
Today’s consumers are more informed and connected than ever before. They seek transparency, sustainability, and personalization in their choices. This trend pushes brands like Chas6d to rethink their strategies.
Social media plays a pivotal role in shaping opinions and trends. Engaging with customers directly allows for real-time feedback and fosters loyalty.
Moreover, the rise of e-commerce changes how consumers interact with products. Instant access means that expectations are higher regarding convenience and service quality.
Understanding these behavioral nuances can help Chas6d anticipate market shifts. Investing in consumer research will be essential for identifying emerging needs.
Brands that listen actively to their audience can innovate effectively. This responsiveness might set them apart from competitors who remain stagnant or disconnected from consumer desires.
Conclusion: Embracing Change and Innovation for a Brighter Future
The future of Chas6d is filled with possibilities. As technology continues to evolve, embracing change becomes essential for growth. Staying updated on trends can guide Chas6d through the complexities of a fast-paced market.
Innovation will be key in adapting to consumer behaviors and preferences, which are constantly shifting. By investing in new technologies and staying attuned to customer feedback, companies like Chas6d position themselves for success.
While challenges may arise, they also present opportunities. Finding creative solutions will allow businesses within this space not only to survive but thrive.
Adapting proactively ensures that as we look ahead, there remains hope for a bright and prosperous journey for Chas6d and its community.
TECHNOLOGY
www aeonscope .net Delivers Results No One Talks About

The Quiet Giant in the Room
In an era where everything is SEO-optimized, influencer-pumped, and algorithm-drenched, some platforms still manage to stay sleekly under the radar—delivering savage results without making a sound. Enter www aeonscope .net, the name that rarely makes splashy headlines, but has the digital underworld buzzing like a Wall Street trading floor on Red Bull.
You won’t see www aeonscope .net parading on TikTok or sponsoring tech expos with neon logos and awkward keynote speeches. It doesn’t need to. This site has cultivated a cult-level following among performance-obsessed marketers, rogue digital entrepreneurs, data analysts, and a new breed of cyber-savvy creatives who value results over noise. And that’s exactly what Aeonscope delivers: results. Quietly. Brutally. Consistently.
So why isn’t everyone talking about it? Because the ones who are in the know want to keep it that way. Let’s break the code.
A UX So Sharp, It Might Bleed
First things first: the user experience on Aeonscope feels less like a SaaS product and more like accessing a secret level in a video game. Everything from the dashboard layout to the data visualization flows like silk dipped in code. No fluff. No pop-ups. No generic clipart mascots.
Just raw intelligence, dressed up in minimalist aesthetics and military-grade performance.
Aeonscope knows its audience. The people who use it don’t need cartoons or tutorials. They need tools that work—and Aeonscope delivers with sniper precision.
Whether you’re optimizing a campaign, diagnosing analytics irregularities, or probing into digital behavior models, the platform responds in real-time. It’s like giving a Ferrari to someone who’s only ever driven Uber. Welcome to the big leagues.
The Core Offering: What It Really Does (That Others Can’t)
Aeonscope’s public-facing features seem tame: trend tracking, audience segmentation, growth projection, performance metrics. Same soup, different ladle? Not quite.
The true magic happens in the sub-features—those little power tools buried inside innocuous dropdowns that whisper “I’ve got what you’re looking for.”
Here’s a quick look under the hood:
-
Neural Predictive Engine™: Not just analytics, but analytics with foresight. Aeonscope doesn’t wait for your KPIs to shift—it tells you what’s about to shift before your competitors can even spell “pivot.”
-
PatternSync Protocols: Tracks user behaviors across platforms and filters out the noise to show why users take action—not just when or how.
-
CloakLayer Encryption: The reason Aeonscope is favored by security-first industries? Its data is so well-shielded, it practically ghosts third-party trackers. We’re talking Fort Knox-level architecture dressed in a UX that feels like a cold breeze on a hot day.
-
Microtrend Surfacing: Think Google Trends on anabolic steroids. Aeonscope doesn’t just catch waves—it sniffs them out in the undertow before they break the surface.
The Real-World Results: Quiet Dominance
Let’s get surgical. Here’s what Aeonscope has quietly done across industries—without any Super Bowl ads or celebrity shout-outs.
🧠 Case Study: Neurotech Startup
A mid-tier neuroscience platform plugged into Aeonscope’s behavioral analysis suite. Within three weeks, it isolated a sub-demographic that was clicking but not converting. Aeonscope mapped content gaps, UX stutters, and time-on-page microdrifts. The fix? Two word changes in a CTA and a slight reposition of a value proposition.
Result: +41% conversion, -18% churn rate. Boom.
🛒 Case Study: E-Com Underdog
A scrappy e-commerce site selling ergonomic furniture (yeah, the sexy kind) used Aeonscope to track post-pandemic shopping psychology. Not just what people were buying—but what they were afraid of. Aeonscope pulled data from trend ripples, Reddit flares, and heatmaps across five continents.
Result: A rebranded anxiety-focused campaign that doubled revenue in 90 days.
📊 Case Study: Finance Firm Flying Below the Radar
Using the Neural Predictive Engine, a boutique investment firm made strategic moves three quarters before the 2024 AI boom hit. Coincidence? Not quite.
Aeonscope had flagged dormant buzz around two keywords on fintech forums and predicted a sector surge. They adjusted accordingly.
Result: A 380% ROI on mid-cap repositioning—and not a single newsletter shout-out.
The Subculture Vibe: Built for the Shadow Elite
Let’s not kid ourselves. www aeonscope .net isn’t for everyone. This isn’t Canva for beginners or HubSpot with a smile. It’s for users who think in loops, flows, and frameworks. The coders who dream in hex. The marketers who write conversion copy in their sleep. The strategists who thrive in the ambiguity between trend and truth.
Aeonscope’s deliberate opacity keeps out the fluff. The brand’s aesthetic leans toward the enigmatic: sleek logins, monochrome palettes, and an almost total absence of hand-holding. It’s not unfriendly—it just assumes you’re ready.
You don’t sign up.
You gain access.
The Psychology of Silence: Why Nobody Talks About Aeonscope
So let’s crack this silence. Why isn’t Aeonscope lighting up LinkedIn thought pieces or X (formerly Twitter) threads?
Three reasons:
-
Power Users Don’t Share Tools
Just like top chefs won’t reveal their secret spice mix, Aeonscope’s top-tier users treat it like a proprietary weapon. It’s not in their interest to evangelize. If anything, they’d rather you don’t find out about it. -
It’s Anti-Hype by Design
Aeonscope doesn’t run affiliate programs or offer discounts. There are no referral codes, no “invite five friends” schemes. That silence is strategic. Aeonscope isn’t chasing virality—it’s cultivating influence. -
It Works Too Well
Platforms that actually work don’t need gimmicks. Aeonscope’s results speak loudest behind boardroom doors, in private Slack channels, and on encrypted Discord servers. The real users are too busy dominating their niche to broadcast their tools.
Aesthetics That Whisper Luxury, Not Loudness
Aeonscope’s visual language is minimalist cyberpunk meets Scandinavian brutalism. Fonts are tight, interfaces crisp, animations sparse but clean. Think if Blade Runner and Muji had a UX lovechild.
But aesthetics here aren’t about showing off—they’re about evoking trust. Nothing screams credibility louder than restraint.
Who Should Actually Use Aeonscope?
Let’s be clear. Aeonscope isn’t plug-and-play for amateurs.
But if you fall into one of these camps, lean in:
-
Advanced Growth Hackers: You’ve played with every growth tool on Product Hunt and you’re hungry for the next frontier. This is it.
-
Behavioral Data Analysts: If mapping audience psychology gives you goosebumps, Aeonscope’s your candy store.
-
Digital Strategists: You juggle cross-platform trends and crave unified dashboards with predictive insights.
-
Elite Freelancers & Boutique Agencies: You need to outperform firms with 10x your resources. Aeonscope evens the playing field and then some.
The Verdict: Why www aeonscope .net Will Stay Underrated (and That’s a Good Thing)
In the flashy, shouty, overshared ecosystem of tools that promise the world and deliver a landing page, www aeonscope .net stands apart.
Not because it’s louder.
But because it doesn’t need to be.
It’s the unsung enabler behind staggering growth. The brains behind the curtain. The quiet architect of breakthrough campaigns and stealth wins.
Aeonscope isn’t for those who follow trends.
It’s for those who build them.
So next time you wonder how that rival brand leapfrogged your numbers overnight, remember: they might just be running Aeonscope in the shadows—and smiling while you guess how.
-

 TECHNOLOGY2 weeks ago
TECHNOLOGY2 weeks agoTop 10 Must-Read Stories from Kristen Archives You Can’t Miss
-

 TECHNOLOGY6 months ago
TECHNOLOGY6 months agoSky Bri Net Worth Revealed: How She Built Her Financial Empire
-

 TOPIC8 months ago
TOPIC8 months agoBasement Renovation Contractors: How They Tackle Structural Issues During Renovations
-

 TOPIC3 months ago
TOPIC3 months ago5 Reasons the //Vital-Mag.Net Blog Dominates Lifestyle
-

 TOPIC1 month ago
TOPIC1 month agoTop 10 Articles from the ://Vital-Mag.net Blog That You Can’t Miss
-

 CRYPTO5 months ago
CRYPTO5 months agoCrypto30x.com Review: Is It the Right Platform for You?
-

 BUSINESS2 weeks ago
BUSINESS2 weeks agoTraceLoans Explained What You Need to Know
-

 BUSINESS4 weeks ago
BUSINESS4 weeks agoDecoding the Kennedy Funding Ripoff Report: Facts vs. Fiction
